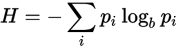13.07 - as you may have seen in the past, at this date, I publish some pretty decent projects, this one isn't an exception and probably will become a subject of a controversy, like it
happened already.
Anyway, the following research (and code) is about the eternal confrontation between order and chaos, specifically between network censorship/filtering and freedom of access, as well as traceability, but also about security.
In order not to complexify an already pretty complex system, let's start from simple things and improve them step by step.
CAN I HAZ ACCEZ?
A simple situation, you're accessing the internet directly (with a router and/or switch) from your device (laptop, PC, tablet, smartphone, etc.) :
This is how the majority of you (unfortunately) access the internet. Well, there are certain advantages, like speed (since no traffic is intentionally modified), simplicity (plug&play) and price (can even be free in some cases). However, there are some obvious disadvantages, like a complete lack of security and privacy. Of course, you still can access some sites over HTTPS, which will provide security (authenticity, confidentiality and integrity), but your ISP or some other attackers or a corporate firewall can see what site you're visiting, for how long and how much data is going (aka metadata), don't even mentioning that if your country/enterprise will decide to block some sites or/and services, you can't access them anymore (using the described schema) :
You still can use another DNS server and even go over
DNSCrypt, but your ISP can still block IPv4 as well as IPv6 addresses and a corporate firewall can force local DNS.
PROXYZ
Some of you might use so-called proxy server, free or paid, which basically routes your web traffic over another server in such a way that your ISP don't handle the packets itself :
This is a pretty common way to bypass censorship and some filtering, although filtering might be problematic since, proxy can force local authentication and redirection, without even speaking about security, especially for "free" proxy servers since, you can't trust them and the traffic still can be unencrypted.
But some of you might have their own servers, in a country with not too many restrictions, which can be used as an encrypted and authenticated proxy server with the help of SSH
Dynamic Port Forwarding :
Putting it to port 443 (HTTPS) will even bypass network filtering and censorship, however, it's only a proxy and not a complete VPN and it can and will be blocked by a majority of corporate WAFs or government DPI since, SSL (used by HTTPS) and SSH are
different protocols.
VPNZ
Speaking about VPN, some of you might also have it :
Which allows to redirect all network traffic transparently through such server, but there is still the problem of protocol difference, although OpenVPN is based on SSL/TLS and support certificates, the traffic order and packets are still different (depending on configuration), thus can be blocked :
So, a solution is to use another software to simulate HTTPS and encapsulate the VPN traffic inside, one of them is
stunnel:
With a proper domain name and certificate, this should work, but you still have to take in count traceability, if you're going to do some stuff that will spark up an interest in your activity since, your VPN provider
will store logs at least on IP level that will lead to you.
H4X0RZ
What hackers commonly do is that they have a "bulletproof" VPN, a server that they buy anonymously (usable cards, crypto, etc.) or just hack and use anonymously (Tor, neighbour WiFi, etc.) :
This is very nice, except that you still have to prevent correlation and don't access Tor directly (which will require
another technique), plus you will lose some speed. An actual VPN isn't required though, you still can have a simple shell, but you suppose to have a server in order to hack properly (like reverse shell) and store loot.
FORGET EVERYTHING YOU JUST READ
Nothing new so far, right? Well, now we will begin the fun part, in short I will do all of the above in a better way without OpenVPN, stunnel and Tor. Moreover, I will secure servers on network perspective, so let's start with this.
First of all, the whole technical configuration can be automated and found on my
GitHub.
Now, we will need iptables on our server to... block all the traffic. Yes, we will block everything which enters the servers (leaving the state-full connections and output/transfer) and yes, this will completely lock it down and make completely invisible on the network. No, I'm not joking. This will ultimately protect from scanning and exploiting the server, "you can't fight what you can't see", the stealth element. I know that you're still wondering, how then we will access the server, except the debug TTY which we may not have in the first place? Well, the answer is knockd,
Port Knocking utility, which will allow a specific IP to connect after a special sequence of ports has been sent to server. This is kind of "security by obscurity", I do agree, but since we will secure everything else, this is an optimal solution InMyHakishOpinion since, you don't waste your resources for fail2ban or other stuff like that. I prefer to use only 80 and 443 ports, which is the minimum network filtering nowadays, and then redirect 443 port to our service.
One of them will be SSH, that should still be on its default 22 port, but I would advise to use only ed25519 asymmetric cryptography for key exchange, public key authentication, and ChaCha20/AES256-GCM symmetric ciphers with Poly1305/SHA256 hashes as those are defacto standards at the moment.
You might think that we will redirect 443 to 22 and you will be right, except that we need our SSL/TLS tunnel, which we will create using...
socat (crypto element), with a custom certificate of course and if you want, you can even generate one using
LetsEncrypt.
At this point, we can freely use our SSH which will bypass WAFs and even switch DPF for proxy effect, but it will be cooler if it was a VPN, right? Well, we will create a VPN using... SSH. No, I'm not joking once again, you can create a
virtual remote tunnel (what is VPN basically all about) using SSH. So with SSH you can have both shell and all your traffic routing through it, cool (with some ipv4_forwarding and NAT post-routing). Right now, our setup looks like this and fully functional :
But we are still missing the "anonymity" part and here's where the "chaos element" comes into place. Well, by chaos I mean
I2P, which we will use to make the connection to a second "bulletproof" server almost untraceable from our first server by simply creating an
indirect tunnel (kind of hidden service) between them :
And yes, the CHAOS server will also have iptables for blocking, but without knockd since we will only allow input for UDP and maybe IPv6 for tunnelling. Such solution will always participate to I2P internal networking and thus making correlation very difficult (which suppose to be the case for VPN as well). We will still need SSH for the very same purpose in proxy mode (shell/VNC/VPN), so basically we are replacing socat with I2P and doing SSH bounce. The main difference is that I2P is made for internal networking, it's like a mini internet with its own crypto and protocols, which is IMHO can be more secure, more reliable and faster than Tor.
Great, the last thing we need to do is to configure all this for our device, in order we can use it and, with some shell scripts and key/certificate sharing everything is done, you can even use it on Android and pretty much any Linux/Unix with some customization, simple and efficient as that (not considering my days of research, problem solving and budget, heh).
As alternative to dropping all the traffic and redirecting using knockd, you can set up your HTTPS web server at the default 443 port and redirect the traffic to SSL:SSH to another port with knockd and socat. Like this, your connection will seem to be legit HTTPS packets with a real HTML site, which will be visible by everyone, whereas it's an encapsulated and prerouted SSH for you.
ALL YOUR DATA ARE BELONG TO US
Wow, amaze haxor, such APT, so hackerish, many pwn, very leet... but can it be defeated? Well, as it is, it can.
First of all, VPN server has to participate in I2P routing in order to make correlation more difficult. Second, you have to store public keys in order to prevent MITM attacks. Third, you shouldn't rely only on knockd and keep your software up-to-date as well as apply "defence in-depth" (like SELinux/grsec/PAX/AppArmor/cgroups). Fourth, even if there is no difference on the protocol level, there will be some regarding packets/bytes/time, so let's do some analysis :
This chart is a simple HTTPS connection to a search engine, for X we have time in seconds and for Y we have the number of packets (red chart) or bytes (black chart). As another example, let's analyze ProtonMail connection :
On the left the ratio of bytes and on the right the ratio of packets, pretty similar characteristics. Now SSH :
As we can see, the SSH connection differs from SSL, both for packets and bytes. Now OpenVPN :
Much more different. How about to compare SSH through socat ?
Well, as you can see, you can change the protocol, but you can't change the data (red - pure SSH, black - over socat). Same goes for VPN :
Note that even if SSH ciphers are better maintained, protocol is more robust and performance is higher, the major bottle-neck is still TCP over TCP, since SSH doesn't support UDP at the moment, which is a bit different topic of discussion, but still a feasible solution.
PHILOSOPHY OF ENTROPY
My point isn't about that order won't ever win versus chaos, or that chaos stands no chance against order, but about the simple fact that none of them can win nor lose. Even if we suppose that the chaos (entropy) is the ultimate destiny of the universe, it will make no sense without order and the fact that the destiny is already determined signifies the presence of order. To put it in the nutshell, nothing is black or white in this world, nothing is determined or uncertain, there is only hope and illusion about either security, either freedom. You can believe me or not, believe that you can believe or not, nothing will matter in the end, but only the fact that you're conscience about your choice at this moment. Entropy is a stable state, so the chaos is order and order is chaos, humans invented it, not universe. Same goes for good/evil, death/life, 0/1 and quantum physics.
Well, I think that I'v kind of leaving my initial topic with such meta-physical-philosophical discussions, without even speaking of all the technical complexity I just explained pretty briefly, so I'll leave you with my "chaos theory" for now.
Remember, the choice doesn't matter, but the fact of choosing does.
Now, think about it all and put my work into the good use :)
Thanks.