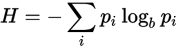Even if TES V Skyrim was released more than 6 years ago, people still play it, people still like it and I found a very interesting and nontrivial way to use it as a decoy to hide information, basically transforming it into a steganographic crypto-container (like TrueCrypt).
You might know from news about MMORPGs espionage, however, this is becoming more than real elsewhere ... I thought that only USA "seek terrorist" in order to do what they want, but it's not a political article.
Perhaps you could use online games in order to have a private chat, it's not a bad idea on a perspective of a decoy, but in a point of security view, there is no encryption and plenty of logs, so if you're going to be under suspicon, it's not going to be private anymore. Nonetheless, how to use offline games as a secure storage? This is what my article is about.
You might wonder - there are already solutions, why bother with another-one? Well, the reason is that I don't agree with the existent. Crypto-containers like TrueCrypt/VeraCrypt/LUKS can be identified and even if you will remove the header (thus adding deniability) you might think that nobody would think that it's an encrypted data, unless you know some mathematics behind cryptology. You see, encrypted data is "random" by nature, a more precise term would be - entropic, and entropy can be calculated, meaning that if you have a huge entropic file (containing "random" data), that would raise a suspicion that may be followed by brute-force that may be followed by cryptanalysis that may be followed by torture. Probably I'm exaggerating for today, but perhaps tomorrow it will be the case.
Anyway, the article suppose to be about games and not about paranoia, so let's do some tests with Skyrim. I have one installed on my Linux with Wine, works not so great, but works. But, do you know what's special about Skryim? Mods, plenty of mods exist for it and if you play Skyrim you probably have dozens of them, but not everybody develop mods, those who do, know their structure, fragmentation and extensions, specifically BSA. Now, let's look at them in the Skyrim's Data folder:
Those are classical Skyrim "mods", which may be included right after the purchase (for some editions). BSA is basically a compressed archive, thus "random" by nature, although it has a deterministic header, it can have a very big size too.
Now, let's look at one of them:
I specifically chose the one with textures because, mathematics. So, let me explain you all this. As ent tool shows, 7.97 out of 8 bits in file looks random, which is 99.7% of them, plus it indicates that the file was indeed well compressed, the chi-squared distribution isn't good though. It also showed some more interesting statistics, but they are less important and I'll have to explain what I already said, to begin, here's the file's bytes distribution:
As you can see, it's not so random as the entropy may show us, but how is that calculated after all? Well, when dealing with IT we often will reference to Shannon's entropy, which indicates how "random" are bytes of a file:
Basically, you would perform a negative sum of probability occurred for each byte by multiplying it by the logarithm (necessary power) in base two of itself.
Encrypted file is 8/8 entropic (which is sometimes more than a randomly generated file), just like a ZIP archive and it's chi-squared distribution is about 290 for 95% to be sure, now about that:
Basically, it's the fraction of the square of the difference between the estimated distribution and the observed one to the estimated distribution.
That is very interesting because, it shows us if there is a big difference between what we observe and what we estimate, that our hypothesis is true with a certain probability. And here is where I'm not really agree with the ent tool because, it doesn't really shows the probability of being certain (50% in the best case according to them), but let's just say that the lower this number is, the more you can be sure that the data are "really random" and as you can see from the screenshot, 67 million is way bigger than few hundreds, thus we will reject the random nature of such distribution.
I know that you still may have some questions about all this, so feel free to make some web searches in order to fully understand such useful math.
That was to say that even if our file is entropic, it may not be randomly distributed.
Besides, as you may notice the content of the header isn't that random, but it begins from a couple thousands bytes:
So, we can copy the first non-random bytes and then append out crypto-container to it, claiming that it's just a mod for Skyrim whereas it's not, and to extract, we just specify the offset for dd (or directly) and decrypt :
Nevertheless, mathematics will show the truth behind such decoy, as you can see even if adding thousands of nonrandom bytes to 500Mb that wouldn't affect the entropy, neither the chi square, thus raising the suspicion for that file and uncovering it.
But, I'll assume that it would be enough in the near future to bypass border controls in some countries.
Of course, it will be preferably to have a whole steganographic OS or a disk, but don't worry, R&D in progress :)
By the way, if you're afraid that somebody someday might decrypt your files, instead of encrypting them, just try to decrypt :) that way you will have to encrypt the files in order to receive their original form (with the last block lost however) :
You might ask me why I didn't publish a tool to make such BSA mods? I won't and discourage everyone to do so for the same reason this article is written - stealthing. The existence of that tool may also make you suspicious and if you have logs of using it, it's game over. The point is to have no trace whatsoever. If you want more details about what I just wrote, you can checkout one of my works.
Finally, even if you're not going to use my technique, I still hope that you learned something interesting and perhaps useful from my article.
That said, let's make Skyrim sneaking "great again" :)